Prerequisites:
- Infisical Cloud account
- Add the secrets you wish to sync to Amplify to Infisical Cloud
There are many approaches to sync secrets stored within Infisical to AWS Amplify. This guide describes two such approaches below.
Access Infisical secrets at Amplify build time
This approach enables you to fetch secrets from Infisical during Amplify build time.
Create a machine identity
Create a machine identtiy and connect it to your Infisical project. You can read more about how to use machine identities here. The machine identity will allow you to authenticate and fetch secrets from Infisical. Set the machine identity client ID and client secret as Amplify environment variables

- In the Amplify console, choose App Settings, and then select Environment variables.
- In the Environment variables section, select Manage variables.
- Under the first Variable enter
INFISICAL_MACHINE_IDENTITY_CLIENT_ID, and for the value, enter the client ID of the machine identity you created in the previous step.
- Under the second Variable enter
INFISICAL_MACHINE_IDENTITY_CLIENT_SECRET, and for the value, enter the client secret of the machine identity you created in the previous step.
- Click save.
Install Infisical CLI to the Amplify build step
In the prebuild phase, add the command in AWS Amplify to install the Infisical CLI.build:
phases:
preBuild:
commands:
- sudo curl -1sLf 'https://dl.cloudsmith.io/public/infisical/infisical-cli/setup.rpm.sh' | sudo -E bash
- sudo yum -y install infisical
Modify the build command
You can now pull secrets from Infisical using the CLI and save them as a .env file. To do this, modify the build commands.build:
phases:
build:
commands:
- INFISICAL_TOKEN=$(infisical login --method=universal-auth --client-id=${INFISICAL_MACHINE_IDENTITY_CLIENT_ID} --client-secret=${INFISICAL_MACHINE_IDENTITY_CLIENT_SECRET} --silent --plain)
- infisical export --format=dotenv > .env
- <rest of the commands>
Service tokens are being deprecated in favor of machine identities.They will be removed in the future in accordance with the deprecation notice and timeline stated here. Generate a service token
Go to your project settings in the Infisical dashboard to generate a service token. This service token will allow you to authenticate and fetch secrets from Infisical. Once you have created a service token with the required permissions, you’ll need to provide the token to the CLI installed in your Docker container. Set the service token as an Amplify environment variable
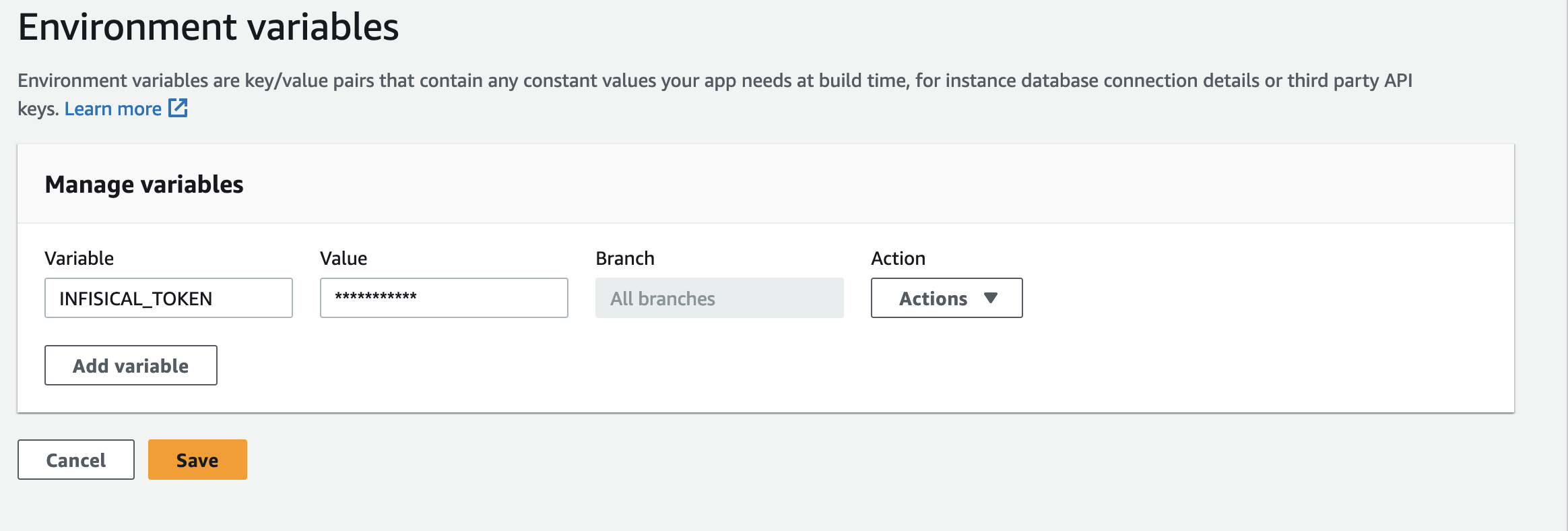
- In the Amplify console, choose App Settings, and then select Environment variables.
- In the Environment variables section, select Manage variables.
- Under Variable, enter the key INFISICAL_TOKEN. For the value, enter the generated service token from the previous step.
- Click save.
Install Infisical CLI to the Amplify build step
In the prebuild phase, add the command in AWS Amplify to install the Infisical CLI.build:
phases:
preBuild:
commands:
- sudo curl -1sLf 'https://dl.cloudsmith.io/public/infisical/infisical-cli/setup.rpm.sh' | sudo -E bash
- sudo yum -y install infisical
Modify the build command
You can now pull secrets from Infisical using the CLI and save them as a .env file. To do this, modify the build commands.build:
phases:
build:
commands:
- INFISICAL_TOKEN=${INFISICAL_TOKEN}
- infisical export --format=dotenv > .env
- <rest of the commands>
Sync Secrets Using AWS SSM Parameter Store
Another approach to use secrets from Infisical in AWS Amplify is to utilize AWS Parameter Store.
At high level, you begin by using Infisical’s AWS SSM Parameter Store integration to sync secrets from Infisical to AWS SSM Parameter Store. You then instruct AWS Amplify to consume those secrets from AWS SSM Parameter Store as environment secrets.Follow the AWS SSM Parameter Store Integration guide
Find your Amplify App ID
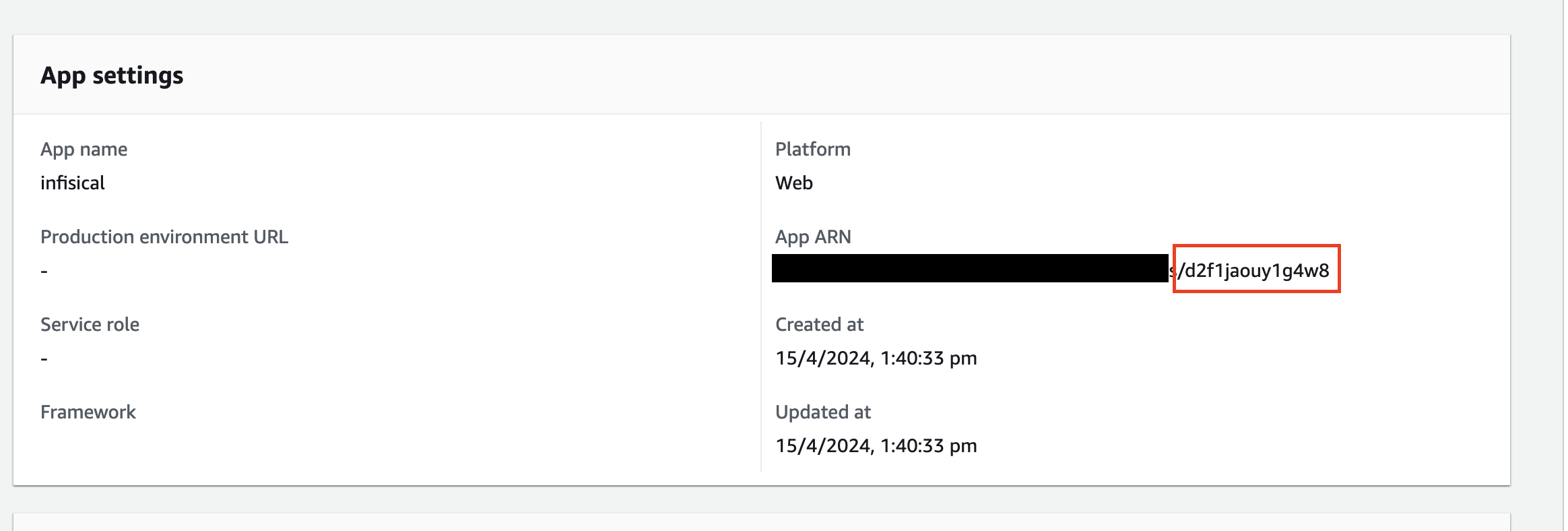
- Open your AWS Amplify App console.
- Go to Actions >> View App Settings
- The App ID will be the last part of the App ARN field after the slash.
Set AWS SSM Parameter Store path
You need to set the path in the format /amplify/[amplify_app_id]/[your-amplify-environment-name] as the path option in AWS SSM Parameter Infisical Integration.
Accessing an environment secret during a build is similar to accessing
environment variables, except that environment secrets are stored in
process.env.secrets as a JSON string.




